It’s time to ditch your VPN
Twingate makes Zero Trust Network Access easy to deploy, even easier to use, and always secure. At first, my initial thought was a bit sceptical, but after validating and testing, I like this new way of VPN connection. I see many opportunities to provide development environments with the necessary security, but as a company, pay a lower bill for a VPN solution only for a development environment.
What is Twingate?
Twingate VPN is a modern, cloud-based VPN (Virtual Private Network) solution that provides secure access to company resources. Unlike traditional VPNs that rely on complicated network configurations, Twingate uses a zero-trust approach that only grants access to authorized users and devices.
The zero-trust approach means Twingate verifies the user’s identity and device before allowing company resources to be accessed. As a result, it eliminates the risk of unauthorized access and reduces the likelihood of data breaches or cyberattacks.
Twingate deploys a cloud-based gateway that acts as a middleman between the user and the company resources. This gateway is responsible for verifying the user’s identity and ensuring that only authorized users and devices can access company resources. In addition, it uses encryption to protect data in transit and ensures that company resources are not exposed to the public internet.
How it works and more documentation?
- Twingate Gateway Deployment: A Twingate Gateway is deployed in the company’s network infrastructure or cloud environment. The Gateway acts as a bridge between users and company resources.
- User Authentication: When users try to access company resources, they first authenticate their identity with Twingate Gateway. The Gateway validates the user’s identity using a zero-trust approach, meaning only authorized users and devices can access company resources.
- Authorization and Access Control: Once the user’s identity is authenticated, Twingate Gateway applies access policies to determine which company resources the user can access. Access policies can be based on user identity, device identity, location, and other factors.
- Resource Access: After the user’s identity is authenticated and access policies are applied, the user can access the authorized company resources. All traffic between the user and the resources is encrypted to protect it from prying eyes.
- Centralized Management: Twingate provides a centralized management console for administrators to manage user identities, access policies, and resource access. This console allows administrators to add or remove users, revoke access, and control access policies.
Overall, Twingate provides a secure bridge between users and company resources, using a zero-trust approach to authenticate users and devices and apply access policies. This ensures that only authorized users and devices can access company resources, and all traffic is encrypted to protect it from prying eyes.
https://www.twingate.com/docs/
Azure VPN Costs vs Twingate costs in Azure
Azure VPN
* only using basic VPN configuration
- Need a lot of components setup in Azure
- Basic VPN solution in Azure
- Hub-Spoke topology allowed
- Cannot stop the services, need to redeploy it
Twingate
* free version in use
- Only need Azure Instances as resource
- Free services
- Hub-Spoke topology allowed
- Need to stop and start services
* Always on costs Twingate 35 euro / month for 1 instance.
How to secure your development environment
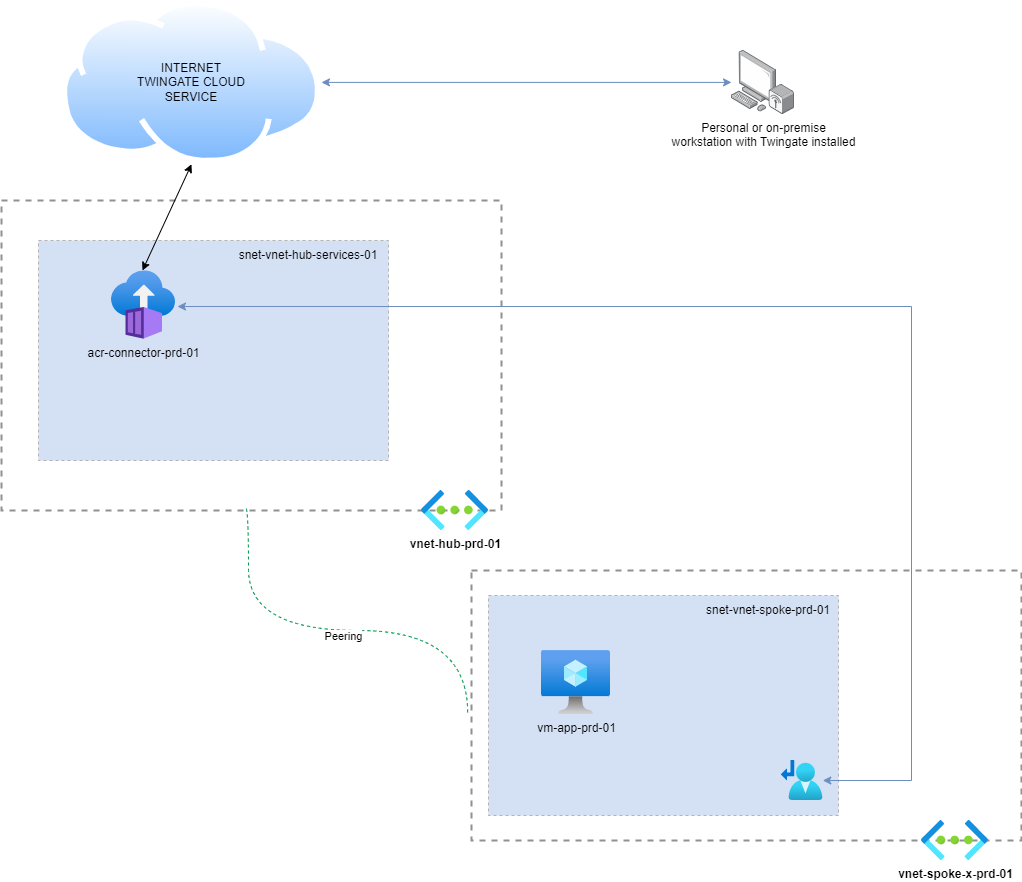
If you choose to work with Twingate, we can set up per development environment one instance. You can secure the network in the Twingate portal and allow access to the correct team members. The members can log in with the client installed on their machine and access only the specific development environment deployed.
Another option is to have a Hub-Spoke topology where you place one or more instances in the hub (connectivity) network to which you connect. Some UDRs (User Defined Routes) are in place to ensure that the network flows correctly. The disadvantage is that every developer can access another network or development environment. You can resolve it by making some teams in the Twingate portal and only allowing specific ranges to some teams. No need for a Firewall because Twingate will cover this. Examples of some security teams are below.
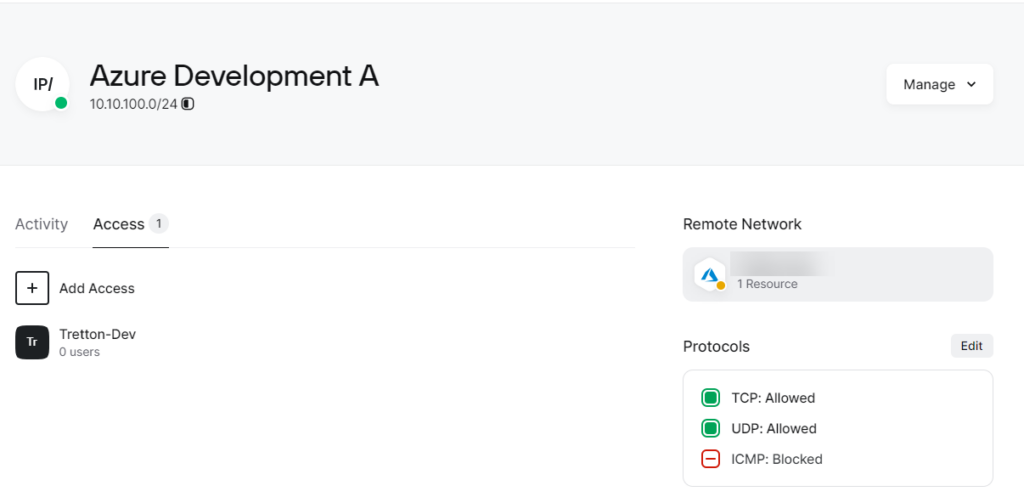
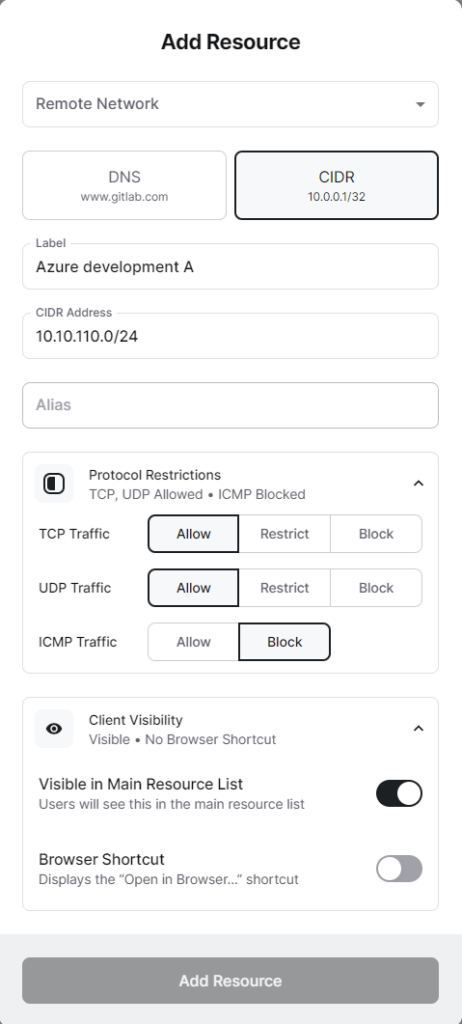
Create a resource or network range
How DNS works for Twingate can be found here:
How DNS Works with Twingate | Docs | Twingate
Conclusion
We can make the following conclusions from testing and validating the Twingate VPN.
- A good and cheaper alternative for development environments
- Enterprise-focused is still being determined, but there is potential to grow and be a full-fledged replacement.
- Very user-friendly and easy to manage
- Always-on VPN with a strong emphasis on security
- You need to authenticate every 4 hours, which can be changed in the settings, but minimal once a day, you need to authenticate the client.
In conclusion: worth a try, especially to better protect development environments and introduce private networking for middle and small companies.